Check::RosKomNadzor - Checking a website against the Roskomnadzor database
Scraper Overview
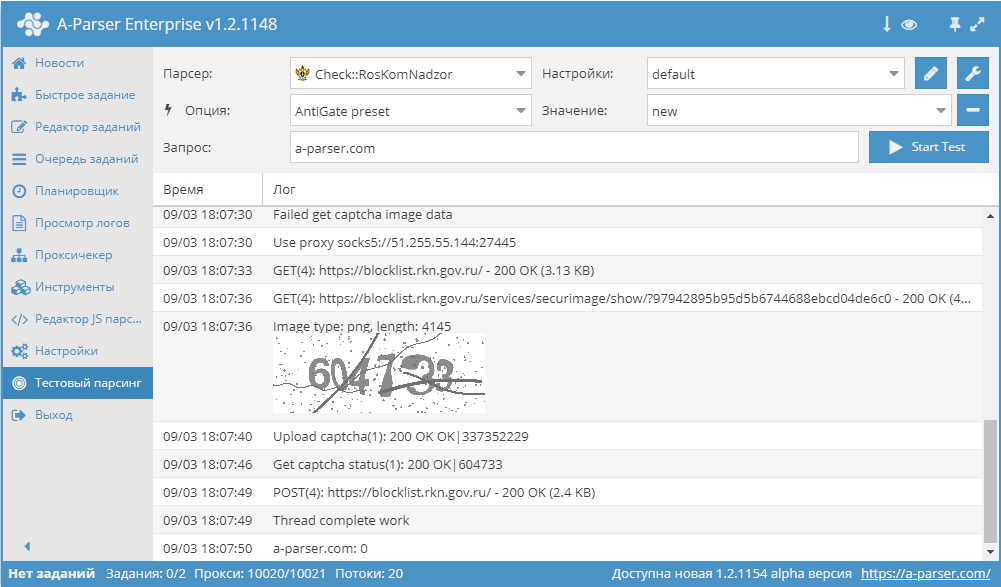
 Check::RosKomNadzor – checks for the presence of a domain in the Roskomnadzor database. Automated collection of all data: date of basis for inclusion in the registry, basis number, authority that made the decision.
Check::RosKomNadzor – checks for the presence of a domain in the Roskomnadzor database. Automated collection of all data: date of basis for inclusion in the registry, basis number, authority that made the decision.A-Parser functionality allows saving the parsing settings of the GooglePlay::Apps scraper for future use (presets), setting a parsing schedule, and much more.
Saving results is possible in the format and structure you need, thanks to the powerful built-in templating engine Template Toolkit which allows applying additional logic to the results and outputting data in various formats, including JSON, SQL and CSV.
Collected Data
The scraper checks for the presence of a domain or link in the site's database.
To run the scraper, you need to configure and connect  Util::AntiGate.
Util::AntiGate.
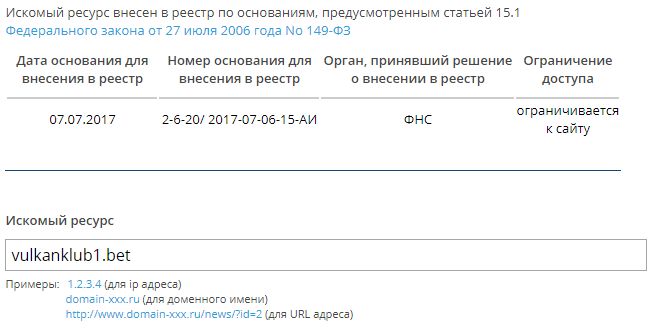
- Checks for the presence of a domain\link in the registry (0 - not in the registry, 1 - is in the registry)
- Date of basis for inclusion in the registry
- Number of basis for inclusion in the registry
- Authority that made the decision for inclusion in the registry
- Access restriction
Use Cases
- Allows checking if websites are in the Roskomnadzor banned database
Queries
As queries, you need to specify the domains of the sites to be checked, for example:
a-parser.com
vulkanklub1.bet
Output Results Examples
A-Parser supports flexible result formatting thanks to the built-in templating engine Template Toolkit, which allows it to output results in arbitrary form, as well as in structured form, such as CSV or JSON
Default Output
Result format:
$query: $exists\n
Example result:
a-parser.com: 0
vulkanklub1.bet: 1
Possible Settings
| Parameter | Default Value | Description |
|---|---|---|
| AntiGate preset | default | Util::AntiGate scraper preset. It is necessary to pre-configure the scraper  Util::AntiGate - specify your access key and other parameters, and then select the created preset here. Util::AntiGate - specify your access key and other parameters, and then select the created preset here. |